Introduction
If you're as excited as me about signing into your Linux server from your Windows machine and completely ditching passwords and private keys stored on your computer in the process then this is the one and true guide for you!I've been wanting to do this ever since I've bought my first two Yubikey NEO keys 4 years ago, but the tutorials on the 'net just weren't working out for me.
PGP seemed scary, over complicated and archaic and I was merrily flaunting my newfound 2FA powers anyway and couldn't be bothered with any of the crypto crud.
Four years have passed and yesterday finally the time has come and I've decided to take the plunge and figure all this crypto nonsense out for good.I will spare you the detailed explanations one might expect when reading crypto articles because frankly it's an unpleasant experience. The tooling is subpar, the terminology is all over the place and I just wanted to get it done without screwing around.So here it is, and by the end of it you should be connecting to your fancy Linux servers from Windows via SSH using PGP keys and Kleopatra like there's no motherfucking tomorrow.
Master key
- Disable any custom firewalls like TinyWall and the like along with any custom anti-virus to prevent weird errors.
Windows Defender and Windows Firewall in their default configurations are fine. - Install Gpg4win from https://www.gpg4win.org/
- I only install GnuPG and Kleopatra (skip GPA, GpgOL, GpgEX and browser integration)
- I install it to a path with no spaces in it, e.g. D:\Programs\Gpg4win
- My version is 3.1.13 (2020-09-04)
- If you had an earlier version of Gpg4win, my tutorial might not work for you so uninstall it and make sure you have at least 3.1.13
- Create a file called gpg-agent.conf under c:\Users\<YOUR_USER>\AppData\Roaming\gnupg\
- Put this in it & save:
enable-putty-support
enable-ssh-support - Insert your Yubikey into a USB slot
- Run Kleopatra
- Tools -> Manage Smartcards
- Hit F5 to refresh
- You should be seeing something like this:
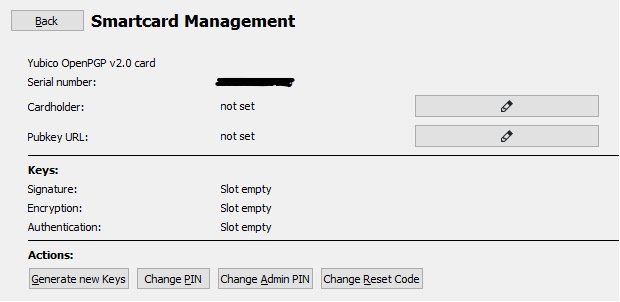
- File -> New Key Pair...
- Create a personal OpenPGP key pair
- Click on Advanced Settings...
- Key Material: select RSA and uncheck +RSA
- Bits:
- YubiKey NEO: 2048 bits
- Any other YubiKey 4 and up: 4096 bits
- Certificate Usage: uncheck everything (Certification will remain checked, that's okay)
- If you want your master key to expire, you can check "Valid until" and give it a date. You can also set this later.
- This is how it should look:
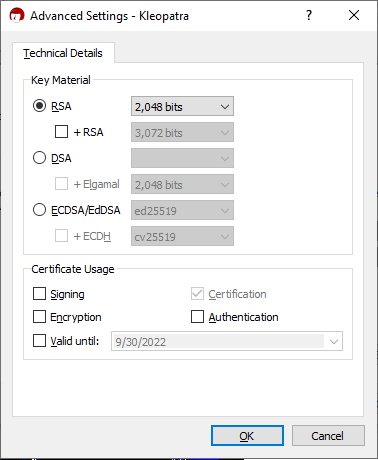
- OK
- You have to enter either your name, email or both. I keep my info private so I just enter Dave as my name and leave email empty. You can change them later.
If you want to use your keys for signing stuff like git commits then you should probably fill both name and email in. - This is how it looks for me:
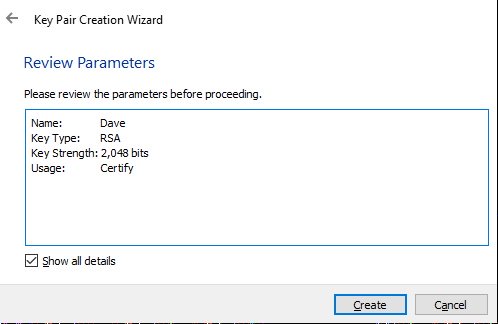
- Create
- Enter a strong passphrase for the key
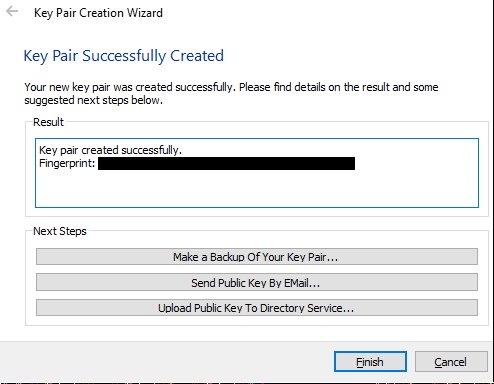
- Click on "Make a Backup Of Your Key Pair..." and save it somewhere safe
- Make sure the extension of the saved file is asc after it's been saved, open the file in notepad and check if it's text and starts with --BEGIN PGP PRIVATE KEY BLOCK--
- Now click "Make a Backup Of Your Key Pair..." again, but this time explicitly give it the extension pgp
- Save the file, open it in notepad and check that it's binary, i.e. not human-readable
- You should now have two backup files of your private key (master key) in the same directory.
- Do _NOT_ upload your public key to a directory service (keyserver) just yet!
- Click Finish
- Your key should now be listed in Kleopatra:
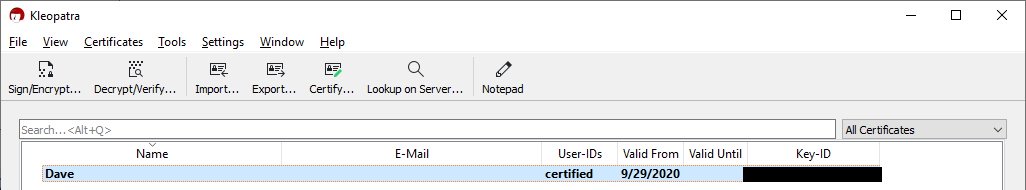
- Click on your certificate to select it
- View -> Details
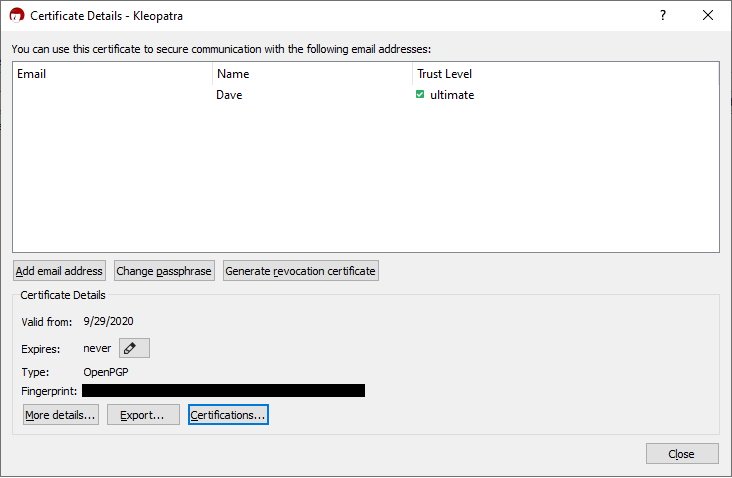
- Click on "Generate revocation certificate" and save the file. It should automatically get the extension rev and the file type should be text.
- Close
- Quit Kleopatra
- Find Kleopatra's icon in the system tray -> right click -> Shutdown Kleopatra
- But this won't kill the underlying gpg-agent process, so launch a command prompt in your GnuPG\bin folder. For me it's d:\programs\gnupg\bin (no spaces) but you've probably installed it elsewhere. The default is C:\Program Files (x86)\gnupg\bin I believe.
gpg-connect-agent KILLAGENT /bye- (You can double check in the Windows task manager if indeed no gpg-agent.exe is running anymore)
Isn't open source fun! No? How dare you.
Brief explainer
A PGP key has 4 possible uses:
- Certification
- Signing
- Encryption
- Authentication
We've set your private key (a.k.a. master key) up to be usable for certification only, that is it's the key that creates subkeys but does nothing else.
Signing and encryption are not necessary for logging in to Linux so I'm putting them into the optional Appendix should you still want to do the whole dance.
In my opinion it would needlessly over complicate things at this point.
So with that out of the way, let's make you an Authentication key!
Subkeys
This is where it gets iiiiiinteresting! If you loathe over complicated procedures and arcane rituals as much as I do then you will absolutely hate all this nonsense - but it is necessary.
Want to log in to that juicy Linux server all by your smart carded self? Then don't give up and read on!
Kleopatra doesn't support the creation of subkeys because that would simply be too useful we all love command line tools.
-
gpg -K- mind the capital K
- You should see a single key with [C] next to it and its long id below:
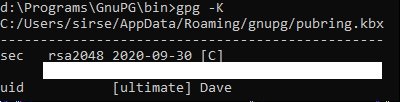
gpg --expert --edit-key <your_key_id>- is either the long id or the long id's last 8 characters
<your_key_id>
- If you enter the wrong id gpg will complain so you can't really mess this up.
addkey- for RSA (set your own capabilities)
8 - to turn the authenticate capability on
a - to turn the sign capbility off
s - to turn the encrypt capability off
e - This should leave you with just the Authenticate capability:
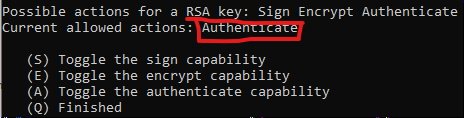
q- Keysize: enter for Yubikey NEO or
2048for any other Yubikey 4 and up4096 - Expiry: I enter (zero) so the key never expires, feel free to enter something else
0 y- again
y - It should ask you for your passphrase and proceed to create the new authentication key
- After that you should be presented with this:
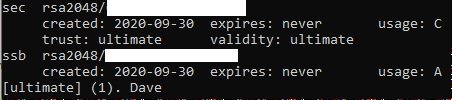
- One key with usage C (the master key) and another with usage A (the authentication key you've just created)
key 1- This should select the auth key and put an asterisk (
*) next tossbso it becomesssb* keytocard3- Enter your passphrase
- Enter the admin PIN which is
12345678 save- This should exit the gpg tool
gpg -K- it's a capital K
- Observe the greater-than sign right after
ssb>
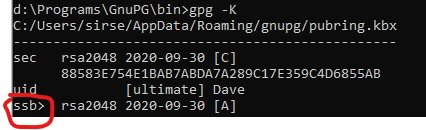
- This means that the auth key has been moved to your Yubikey from your computer
gpg --edit-cardadminpasswd1- First, enter the existing PIN which is then enter in a custom PIN which is at least 6 characters long
123456 3- First, enter the existing admin PIN which is then enter in a custom admin PIN which is at least 8 characters long
12345678 qquitgpg-connect-agent KILLAGENT /bye- Launch Kleopatra
- Select your certificate
- Click on File -> Export...
- Save it to a directory as-is
- Click on File -> Export... again
- Save it with the pgp extension to the same directory
- There should be two files in that directory now: one with the extension asc, another with pgp. Asc is text, pgp is binary.
- These two files both contain your public key
- BACKUP your private key: File -> Export Secret Keys..., save one in the default extension (asc) and one in pgp
- Now it's time to DELETE all the keys from your computer!
Since you've made a backup of your private and public key you need not worry. - Select your certificate in Kleopatra
- Certificates -> Delete
- Confirm all the many deletion prompts
- Quit Kleopatra
- Find Kleopatra's icon in the system tray -> right click -> Shutdown Kleopatra
gpg-connect-agent KILLAGENT /bye
Public key
- Now, upload your public key to a server on the internet.
Do _NOT_ upload your public key to a directory service (keyserver) just yet!
You need to upload the .asc file (the one that is text) gpg --edit-cardadminurl- Enter your public key's URL
- Enter the admin PIN (the default was 12345678 but you've changed it!)
fetchquit- Now to make your Linux server aware of your new keys!
gpg --export-ssh-key <your_key_id>- This will print out the public key in SSH format
- Log in to your Linux server
- Insert the above SSH public key into your ~/.ssh/authorized_keys file and save it
- Restart your Windows PC!
- Now's the time to test it all out!
- Close Pageant if it's running
gpg-connect-agent KILLAGENT /bye- Run Kleopatra
- Try & log in via PuTTY and it should just work
WOOHOO IT WORKED, FANTASTIC AMIRITE!!!
Great! Now that your main key is out of the way, let's propagate this goodness unto all your additional Yubikeys.
It's important to have at least one backup key, though I wouldn't blame you if you just wanted to murder anyone who ever mentions PGP again at this point.
Additional Yubikeys
- In Kleopatra: File -> Import...
- Find the backup you've made of your private key and import it
- Say Yes when asked if it's your key
- Ok
- Double-click the certificate -> More details... -> there should be two entries: one with usage Certify, another with usage Authenticate
- Close all the windows and Kleopatra itself
- Find Kleopatra's icon in the system tray -> right click -> Shutdown Kleopatra
gpg-connect-agent KILLAGENT /bye
Repeat for each additional Yubikey:
- Plug in the next Yubikey you wish to use to authenticate to Linux
gpg --expert --edit-key <your_key_id>addkey- for RSA (set your own capabilities)
8 - to turn the authenticate capability on
a - to turn the sign capbility off
s - to turn the encrypt capability off
e q- Keysize: enter for Yubikey NEO or
2048for any other Yubikey 4 and up4096 - Expiry: I enter (zero) so the key never expires, feel free to enter something else
0 y- again
y - It should ask you for your passphrase and proceed to create the new authentication key
- Now there should be as many keys with usage: A as the number of Yubikeys you've added so far.
- The keys are zero-based, so the first key is 0, the next is 1, the third is 2, etc.
key <last_key>- e.g. if this is for your second Yubikey
key 2
- e.g.
- This should select the last auth key and put an asterisk (
*) next tossbso it becomesssb* keytocard3- Enter your passphrase
- The admin PIN is still since this is a new Yubikey
12345678 save- This should exit the gpg tool
gpg -K- it's a capital K
- Observe the greater-than sign after all the
ssb> - This means that the auth keys have all been moved to your Yubikey from your computer
gpg --edit-cardadminpasswd1- First, enter the existing PIN which is then enter in a custom PIN which is at least 6 characters long
123456 3- First, enter the existing admin PIN which is then enter in a custom admin PIN which is at least 8 characters long
12345678 qquit
Once you're done with all your Yubikeys, it's time to re-export the public key so it's amended with all the new authentication keys sitting on your army of Yubikeys.
You will have to do this every time you decide to add more keys to your keychain in the future!
gpg-connect-agent KILLAGENT /bye- Launch Kleopatra
- Select your certificate
- Click on File -> Export...
- Save it to a directory as-is
- Click on File -> Export... again
- Save it with the pgp extension to the same directory
- There should be two files in that directory now: one with the extension asc, another with pgp. Asc is text, pgp is binary.
- These two files both contain your public key
gpg --export-ssh-key <your_key_id>- This will print out the public key in SSH format
- Log in to your Linux server
- APPEND your new public key to your authorized_keys file and save it (all the keys should be on their own line as usual)
- BACKUP your private key: File -> Export Secret Keys..., save one in the default extension (asc) and one in pgp
- Now it's time to DELETE all the keys from your computer! Since you've made a backup of your private and public key you need not worry.
- Select your certificate
- Certificates -> Delete
- Confirm all the many deletion prompts
- Quit Kleopatra
- Find Kleopatra's icon in the system tray -> right click -> Shutdown Kleopatra
gpg-connect-agent KILLAGENT /bye- Now, re-upload your public key to a server on the internet.
Do _NOT_ upload your public key to a directory service (keyserver) just yet!
You'll need to upload the .asc file (the one that is text)
Repeat for each of your newly added Yubikeys:
- Insert the Yubikey
gpg --edit-cardadminurl- Enter your public key's URL
- Enter the admin PIN (the default was 12345678 but you've changed it!)
fetchquit
Log in to your Linux server with your newly added Yubikey:
- Close Pageant if it's running
gpg-connect-agent KILLAGENT /bye- Run Kleopatra
- Try & log in via PuTTY and it should just work
Lastly, switch your custom firewall and anti-virus software back on and check if everything still works.
Now merrily use your newfound PGP+GPG+SSH+Yubikey+Kleopatra powers to log in and out of any of your Linux servers as you please!
If after 3 days you still find everything in order, consider uploading your public key to a keyserver.
Don't do so before the 3 days are up! It gets messy once you have to start revoking keys because you just wanted to test something.
The only thing required from now on other than a Yubikey is that Kleopatra is running. You can remove any keys you still have in Kleopatra, e.g. your public key since you don't need anything for authentication - everything is on your Yubikeys or in backup files on your computer.
Note that your master key only exists in backup file form - which is okay. If you want to be extra paranoid, you can move it to a pen drive that you keep in a safe or what have you. Don't copy it to a Yubikey though - if anything happens to it (gets lost, stolen, damaged) you're screwed.
There are other tutorials on the 'net that use gpg-agent or gpg-connect-agent instead of Kleopatra but I haven't been able to get them to work. Kleopatra uses gpg-agent under the hood and seems to supply all the required configuration parameteres, settings and directories automagically. If it ain't broke don't fix it!

Hope this was helpful, enjoy all this nonsense and brag about it to your friends!
If I've done something stupid let me know in the comments.
References
https://suchsecurity.com/gpg-and-ssh-with-yubikey-on-windows.html
GPG and SSH with Yubikey on Windows
Newsletter
If you are interested in upcoming tutorials and articles, subscribe to the newsletter below:

